Cyber Security with micro:bit

This lesson has been designed as an introduction to the concepts of:
- encryption
- decryption
- protecting information
and does so by using the in-built features of the BBC micro:bit and it's block-based coding website: makecode.microbit.org
_________________________________________________________
The following is our slide deck that can be used to introduce this activity to your participants:
Protecting Information

Cyber security is the protection of information on computers and networks.
We use computers for storage and transmission of data in all professions and everyday life.
Data on our networks can be sensitive or personal and so it needs to be kept secure.
When we protect information we balance the following;
Confidentiality
- Securing against unauthorised access to information or devices.
- We do this by requiring passwords to access our devices or applications, determining application permissions, configuring social media privacy settings. You will see the websites we visit have the lock symbol, or https which indicates the connection is secure.
Integrity
- Protection against tampering or unauthorised modification.
- Think of when you update records or data on systems, after login the system will track alterations and who made them.
Availability
- Accessibility to those who legitimately require access.
- For example you require access to software to do your job, customers need access to the websites or other software.
It is important to maintain a balance between confidentiality, integrity and availability.
You can secure confidentiality and integrity by unplugging the network, however then you have no availability.
Conversely you can create full availability by posting everything online, but then you have no confidentiality and increased vulnerability.
The BBC micro:bit
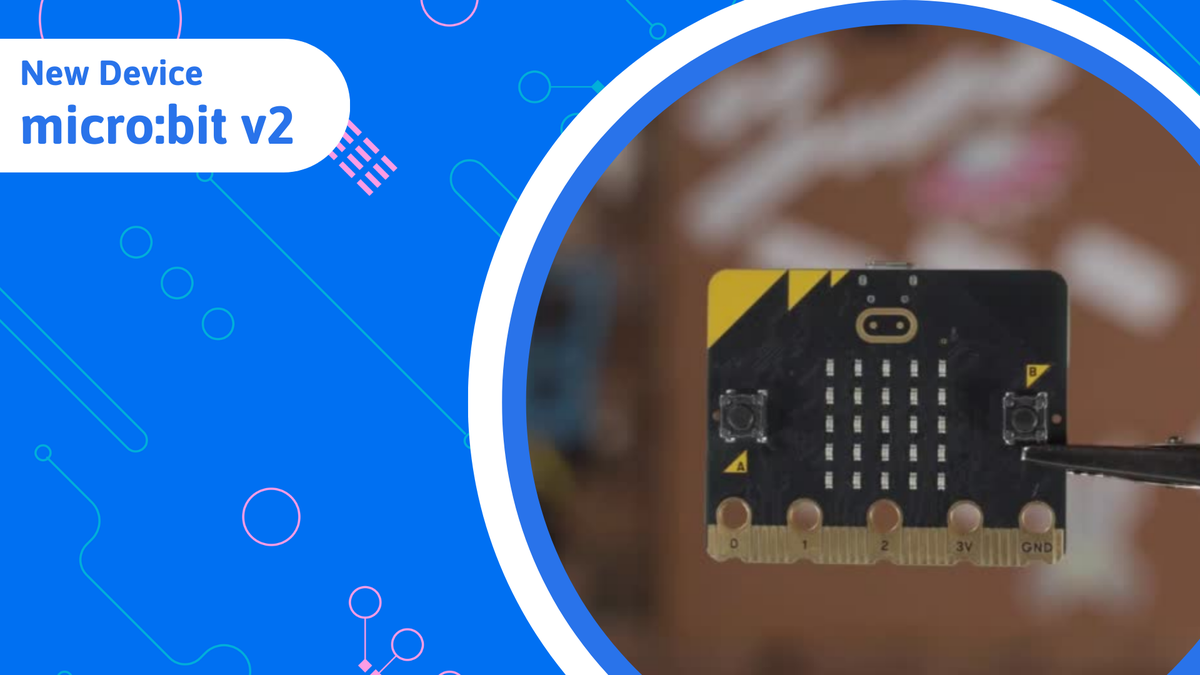
The micro:bit is a computer, small enough to hold in your hand, with all sorts of features you can use to interact with the world. We can even connect the micro:bit to other pieces of hardware to do even more things.
- The micro:bit has a small display on the front, made of 25 small LEDs. We can find LED lights in all sorts of places. LEDs are useful because they don't get hot like other kinds of light bulbs, and they’re quite efficient, which means that they don’t use very much electricity to produce a lot of light.
- The micro:bit features 2 buttons, a capacitive touch sensor and a microphone for user interaction and input.
- The micro:bit also features an in-built speaker, an accelerometer, a compass and battery and USB ports. This robust, compact and diverse little device has a broad range of uses when it comes to teaching and learning about digital technologies, coding and the interactivity between it all.
Ciphers

Ciphers are tools used for disguising or revealing plain text.
They can encrypt or decrypt messages and have been used for thousands of years.
We use them to make information unreadable for a third party who has intercepted a communication.
Primitive cyphers such as Caesar Cypher simply swapped one letter for another further along the alphabet. Over time cyphers have become more advanced, it’s likely you would have heard of the 'enigma' used by Germany in WW2 which was immensely difficult for the allies to break.
Our modern computing gives us the ability to create powerful ciphers, which is useful as information is constantly being transferred over the internet and encryption is used to protect it.
You can find out more about cryptography and ciphers here: https://inventwithpython.com/hacking/chapter1.html
You can also use a virtual Caesar cipher wheel from your web browser here: https://inventwithpython.com/cipherwheel/
You can print your own Caesar cipher wheel here:
Caesar Cipher Template
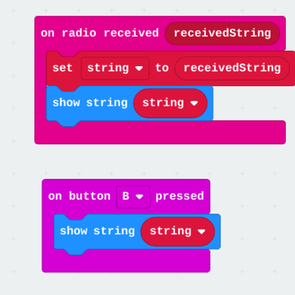
Sample Cyber Security code
Here is the code to be used in MakeCode and on the BBC micro:bit for this activity:
View resourceCode Block Explanation
Here are some brief explanations on the code blocks we will be using:
1 - On start
2 - Show String
3 - On Button Pressed
4 - Set Variable to
5 - Radio Set Group
6 - On Radio Received String
6 - Radio send string
1.
When you place code blocks inside of the ON START block, those blocks will run one time, once the program begins. Then those blocks will stop. This is different to the FOREVER block, in which, code blocks placed inside the forever block will run over and over again, once placed inside.
2.
In computer programming, we use the word ‘string’ to refer to data that is represented as a series of letters, punctuation, and numbers. A string can be a word, a sentence, a series of numbers, or any combination of those. We can show words on the micro:bit display by controlling which LEDs are turned on. If a word or sentence is too large to fit on the display then it will scroll from left to right.
3.
The micro:bit has two buttons built into the front of the board. Buttons are an input. Inputs let us detect something in the real world, which we can then use to trigger an action in our code. Code blocks placed inside the ‘On Button Pressed” block will only run once that button is pressed. The code will run once and will stop unless the button is pressed again.
4.
Variables are a way for our program to remember pieces of information that we can either recall later, or change over time. We can use a variable to store a number or a string.
5.
There are many radio signals being sent around constantly. So we can use the ‘radio set group’ block to give your micro:bit radio a group number. Multiple micro:bits with the same radio group number will communicate with one another and will ignore messages from micro:bits in other groups. This is similar to changing stations on a car radio. There are multiple available at all times, but if you’re all tuned into the same station, you can hear the same message at the same time.
6.
The ‘radio send string’ is similar to the ‘show string’ block, but it will send the string over the radio group you have set. The ‘on radio received string’ block is similar to the ‘on button pressed’ block in the way that code blocks that are placed inside this block will be activated when the radio receives a string.